Anti-Israel hackers release info on over half of all FBI employees
Hacked again, but what have we learned?
Following through with a threat made last week, a group of hackers released data pertaining to as many as 30,000 federal government employees.
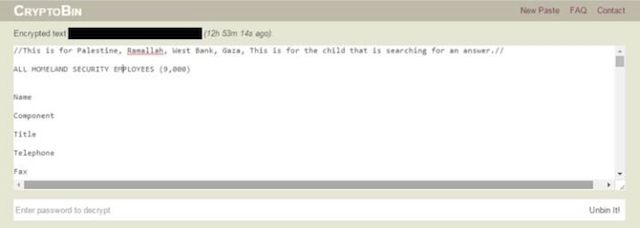
Hacktivists released the information in two waves via a Twitter account by the name of @DotGovs. The data was posted on the encrypted text-sharing website by the name of Cryptobank. The first release took place place shortly after kickoff on Super Bowl Sunday and included a directory of names, job titles, and contact information of 9,355 employees of the U.S. Department of Homeland Security. The second directory was released on Monday and contained subsequent information on 20,000 employees of the FBI. This is more than half of FBI personnel.
Tweets from the @DotGovs account were filled with pro-Palestine hashtags. One tweet was directed towards the U. S., saying the hackers would not stop “until they cut relations with Israel.”
ALL https://t.co/JVNmAdiVAm EMPLOYEES (9,000) NAMES, TITLES, PHONE NUMBER, STATE, EMAILhttps://t.co/gv82WHUp5E#FreePalestine
pass is lol— penis (@DotGovs) February 7, 2016
20,000 FBI EMPLOYEES NAMES, TITLES, PHONE NUMBERS, EMAILS, COUNTRYhttps://t.co/c5mvY49P8S password is lol#FreePalestine — penis (@DotGovs) February 8, 2016
DOJ spokesman Peter Carr said the department “is looking into the unauthorized access of a system operated by one of its components containing employee contact information.” In a statement, Carr said the “unauthorized access is still under investigation; however, there is no indication at this time that there is any breach of sensitive personally identifiable information.”
A look at the leaked files reveals that the information was not publicly accessible and may have been quite sensitive. “The database of FBI staff appears to contain every employee up the the surnames beginning ‘Je’ in the alphabet,” the Telegraph said. It also exposes 1,797 special agents, a task force deputy director, among several others.
Some of the employee information in the leaked files, however, do appear to be outdated. “The information listed included phone numbers and email addresses for individuals who have not worked for DHS in years,” the Telegraph reports. Though the list is believed to be genuine, some of the DHS employee listings included job titles that have since been renamed. The DOJ staff directory also appeared to be somewhat dated. For example, an employee hired by DHS in 2013, for example, was not found in the leaked directory. Several phone numbers, however, did correspond to the names listed while some went through to general FBI switchboard operators.
Earlier last week, the hacker reached out to Vice’s Motherboard with his plans and explained how he had accessed the network:
“The cybercriminal reached out to Motherboard through an apparently compromised DOJ email account earlier last week, and claimed to have obtained the stolen data by compromising that account and then using it to access a DOJ portal.
After tricking a department representative into giving him a token code to access the portal, the hacker claimed he used the compromised credentials to log into the portal, where he gained access to an online virtual machine. From here, the cybercriminal was presented with three different computers to access, he said, one of which belonged to the person behind the compromised email account. The databases of DHS and FBI details were on the DOJ intranet, the hacker said.”
“So I called up, told them I was new and I didn’t understand how to get past [the portal]. They asked if I had a token code, I said no, they said that’s fine – just use our one.” The hacker said he then logged in, clicked a link that gave him access to a virtual machine, and proceeded to enter the email and pass code information pertaining to the DOJ email account he had already hacked. At that point, the hacker said he had the option of three different computers to access, one of them being the work computer of the person behind the DOJ email account. According to the hacker, both DHS and FBI databases were located on the DOJ intranet.
The hacker would not elaborate on how he obtained the ability to log into the government email address in the first place.
top security by @TheJusticeDept here!!! pic.twitter.com/fIt4GIf6pJ
— penis (@DotGovs) February 8, 2016
The breach comes after the embarrassing and immeasurably damaging hack on OPM, the agency that stores employee information of the federal government. Another hack came to light earlier this year when Juniper networks announced unauthorized code had been written into communications software used by several government agencies. Whether work of the @DotGovs group has any link to these breaches has yet to be determined.
Michael L. Adams, an information security expert and former employee at the U.S. Special Operations Command criticized the government for its seemingly repeated failure to protect government data. “What has anybody in the United States learned?” Adams said. “This is not one hack. This is an ongoing hack against the United States, whether its from one or more actors is unknown.”
 DONATE
DONATE
Donations tax deductible
to the full extent allowed by law.








Comments
No big deal.
Let Hillary handle it.
She will tell them that “we will not tolerate their cyber theft and their cyber evasiveness.”
Problem solved.
Right?
“The hacker would not elaborate on how he obtained the ability to log into the government email address in the first place.”
Anti-Israel is simply dog whistle for pro-muslim, and this vile administration is rife with that policy.
Don’t worry. Your data is safe.
Simple.
We either make sure our secrets are secure and make sure our opponents secrets are safe or we make sure there are no secrets.
We all use the same system and the same software, have mostly the same knowledge.
Politicians who argue that we should put backdoors in encryption that we can use also argue that we put backdoors in encryption that they can use. There is no distinction.
Put another way – if government can read electronic communications, then so can everyone else.