Ukraine, Russia, U.S. Affected by Latest Cyberattack
The ransomeware attacked Ukraine’s Chernobyl nuclear site.
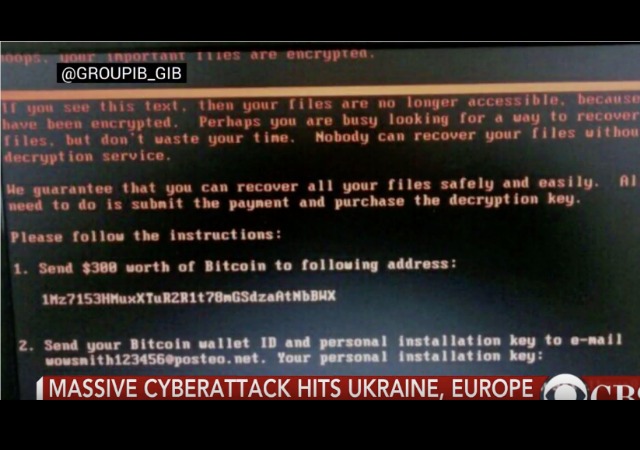
The Petya ransomeware took off yesterday across the globe, affecting state-owned and private businesses in Russia, Europe, and the U.S. The BBC has now reported that it “may have started via corrupted updates on a piece of accountancy software.”
The ransomeware hit Ukraine hardest since it attacked the country’s “power grid, banks and government offices” and disrupted some flights at Kyiv’s Boryspil Airport. Other companies hit included pharmaceutical giant Merck and Russia’s state owned energy company Rosneft.
Petrwrap/Petya Ransomeware
Fox News reported that cybersecurity experts “have been scrambling to identify the specific type of ransomeware deployed and its origins.” Kaspersky Lab researcher Costin Raiu provided some insight on Twitter:
Petrwrap/Petya ransomware variant with contact [email protected] spreading worldwide, large number of countries affected.
— Costin Raiu (@craiu) June 27, 2017
So far, 7 payments in the wallet associated with the [email protected] ransom. pic.twitter.com/HO0VcCgENO
— Costin Raiu (@craiu) June 27, 2017
Kaspersky Lab has identified “more than 2,000 attacks.” The software only attacks computers that use Microsoft Windows.
Remember, ransomeware is software that holds the data in a computer hostage until a ransom is paid. From SecureList:
The malware waits for 10-60 minutes after the infection to reboot the system. Reboot is scheduled using system facilities with “at” or “schtasks” and “shutdown.exe” tools.
Once it reboots, it starts to encrypt the MFT table in NTFS partitions, overwriting the MBR with a customized loader with a ransom note. More details on the ransom note below.
Bogdan Botezatu at Romanian cybersecurity firm Bitdefender explained how it’s spread. From Fox News:
He said that it was likely the ransomware is spreading through a “wormable exploit” – cybersecurity lingo for a program that can spread automatically across a network without the need for human interaction. Worms are particularly feared because they can spread rapidly, like an extremely contagious cold.
A Vaccine and Cause
The BBC also reported that experts have found a “vaccine” for the attack, but could “not find a so-called kill switch that would prevent the crippling ransomeware from spreading to other vulnerable computers.”
Experts think that the attackers used this ransomeware as “a front for causing wider disruption” since they only asked $300 ransom, which is a small amount.
As mentioned above, experts believe the accounting program MeDoc, popular in Ukraine, caused the outbreak. This could be why it hit Ukraine the hardest. MeDoc has denied it, but others explained why. From Business Insider:
The company denied any accidental involvement with the attack on its Facebook page, but Microsoft, security firm Talos, and Ukraine’s own national cyber security department pinned the blame on the software.
Microsoft wrote: “Although this vector was speculated at length by news media and security researchers—including Ukraine’s own Cyber Police — there was only circumstantial evidence for this vector. Microsoft now has evidence that a few active infections of the ransomware initially started from the legitimate MeDoc updater process.”
MalwareTech, the British security researcher who halted the spread of WannaCry, added that it was likely MeDoc was hacked, then its software used to spread the malware to any PC using its accounting service.
He added that unlike WannaCry, there was no “kill switch” — a catch-all solution that would stop the malware.
He wrote: “Although some companies have claimed to have found a kill switch, this is nothing more than PR as the so called “kill switch” is only activated by modifying files on your own system (which can be done to stop most malware) and is not doable remotely like the WannaCry was.
He added: “Furthermore … it’s unlikely the Petya ransomware is still spreading and the damage has already been done, thus a kill-switch would be futile.”
Ukraine
As I said before, the ransomeware hit Ukraine the hardest. From The Kyiv Post:
In Ukraine, the attack has affected state-owned Oschadbank, private Ukrgazbank, energy companies Kyivenergo and Ukrenergo, national telecommunications operator Ukrtelecom, mobile carrier Lifecell, postal companies Ukrposhta and Nova Poshta, Kyiv Boryspil International Airport, DIY chain Epicenter, petrol retailers, and several media companies, including Channel 24 and Korrespondent news website.
Most of the affected companies had to stop or limit their services due to the attack.
The computers of the Cabinet of Ministers of Ukraine were infected with the virus, too, according to Deputy Prime Minister Pavlo Rozenko, who published a screenshot of one of the computers with a black screen and hackers’ warning.
Some of our gov agencies, private firms were hit by a virus. No need to panic, we’re putting utmost efforts to tackle the issue ? pic.twitter.com/RsDnwZD5Oj
— Ukraine / Україна (@Ukraine) June 27, 2017
Officials confirmed that the malware infected the “radiation monitoring system at Ukraine’s Chernobyl nuclear site.” They shutdown the system and employees had “to use hand-held counters to measure levels.” From AFP:
“Due to the cyberattack, the website of the Chernobyl nuclear plant is not working,” said Ukraine’s exclusion zone agency which oversees the Soviet plant that exploded in 1986 and is now surrounded by an uninhabited contaminated zone.
“Due to the temporary shutdown of the Windows system, the radiation monitoring of the industrial area is being done manually,” the agency said on its website.
“That means that our measurers go out with hand-held meters on the Chernobyl plant like it was decades ago,” a spokeswoman for the agency, Olena Kovalchuk, told AFP.
Microsoft Ukraine has told the country that the latest updates will protect computers from the ransomeware if they’re up to date.
Officials said the Bitcoin wallet connected to the malware “has received 13 transactions” from within the country.
Russia and Europe
The malware attacked Russia’s energy company Rosneft, steelmaker Evraz, and the country’s biggest bank. From The Wall Street Journal:
Russia’s state-controlled oil company, PAO Rosneft, said it was under a “massive hacker attack” that could have serious consequences but didn’t affect its oil production.
Rosneft, the world’s largest publicly listed oil company by production, said it had contacted law-enforcement authorities about the attack. The company’s website was down on Tuesday, but its official Twitter accounts spread news of the attack.
The company said it had recently switched to a different oil reserve-control system, so “neither oil production nor preparation processes were stopped.”
Dutch shipping giant A.P. Moller-Maersk also fell victim to the malware. Basically, anything that comes to America on a boat usually comes via Maersk. From The New York Times:
The IT breakdown could extend across the company’s global operations, a spokeswoman said, but could not say how Maersk’s operations were impacted.
Continue reading the main story
With a fleet of more than 600 container vessels, Maersk is the world’s biggest shipping company with a market share of around 16 percent. The company handles around 25 percent of all containers shipped on the key Asia-Europe route.Maersk’s port operator APM Terminals was also hit, with Dutch broadcaster RTV Rijnmond reporting that 17 shipping container terminals run by APM Terminals had been hacked, including two in Rotterdam and 15 in other parts of the world.
The RTV report said computers were infected by ransomware that encrypted hard drives at APM Terminals.
America
Pharmaceutical giant Merck also confirmed the ransomeware attacked its systems.
We confirm our company's computer network was compromised today as part of global hack. Other organizations have also been affected (1 of 2)
— Merck (@Merck) June 27, 2017
We are investigating the matter and will provide additional information as we learn more. (2 of 2)
— Merck (@Merck) June 27, 2017
The ransomeware also got to a hospital in Pennsylvania. From CNBC:
A spokeswoman for Heritage Valley Health System says the attack Tuesday is affecting the organization’s entire health system and employees are working to ensure safe patient care continues.
Heritage Valley is a $480 million network that provides care for residents of Allegheny, Beaver, Butler and Lawrence counties, in Pennsylvania; parts of eastern Ohio; and the panhandle of West Virginia.
 DONATE
DONATE
Donations tax deductible
to the full extent allowed by law.








Comments
this is attempted nuder by proxy and needs to be dealt with accordingly. isis on steroids – these killers -be they teens or octogenarians need to be made a public example of.
no civilization can survive this onslaught.
WHY is a nuclear power plant on the internet?
They functioned before the internet age.
So why are they on the net?
Can our leaders really be this daft?
Because it’s not a fully closed system, and every so often, you want someone off-site to be able to look at what your computers/ switches/ control systems are doing, and consult, without having to fly half-way across the planet. Also, merely the addition of data, unless it’s programmed onto the system manually would itself open a breach for something invasive to get in (the laptop plugged in or the USB stick with the analysis programming).
Separately, think about the office staff, the managers, the HR professionals, Payroll, AR/AP, the maintenance staff (people ordering mops and buckets and the 1000s of other basic items necessary for any functional large business on a day to day basis).
EVERYTHING is done via internet these days. Gone are the days when you would pick up the phone and call a call-center and place an order.
The computers controlling the individual switches are just on a more-secure portion of that network. Building a completely SEPARATE set of networking into a structure just creates more failure points in the infrastructure.
so people can monitor w/o danger.
its not like its operating anymore…
https://www.theregister.co.uk/2017/06/28/petya_notpetya_ransomware/
been deploying the “vaccine” across the few domains I manage.
can be done using group policy or a management program
thiis spreads by a multitude of vectors and is (potentially) worse than wannacry even with smb v1 disabled.
Ukraine, Russia, US affected…
A close association, but was there collusion?