Hamas Honeypot Trap Exposed
Trying to get soldiers to download virus-apps through Facebook come-ons.
Honeypot traps are in the news after the CNN-Buzzfeed Trump-Russia fiasco.
What’s a honeypot trap? Seriously, haven’t you read any spy novels? It when an intelligence agency offers up honey (a girl, boy, whatever) to a target, who then partakes of the honey not knowing the event is being filmed for future blackmail. The trap can be things other than honey (like luring the target into some other financial or criminally compromising position).
Having traveled extensively and studied in the Soviet Union, I know that various traps were set even for lowly students.
Like the time in 1979 at a Tallinn (Soviet Republic of Estonia) nightclub where fellow-American students and I were waiting outside in line, when a car pulled up. Two men approached us in a friendly manner, and whisked us past the proletariat waiting in line into the club, where we were given a prime table to share with them. I acted as translator since I was the only fluent Russian speaker. The men spent most of the night trying to get us to exchange Rubles for Dollars — illegal in the Soviet Union unless done through a government exchange. I spent most of the night politely telling them No. I’m not sure what use they would have made of it, or maybe I was just paranoid, but yes, I had already read spy novels so I wasn’t taking any chances.
A Hamas honeypot trap scheme was just disclosed by the Israelis. Who knows how long the Israelis knew about it — they may have used it to identify Hamas operatives in a reverse-honeypot (I just made up that term). The purpose of the honeypot trap was to lure soldiers into downloading virus-infected apps which would turn their cell phones into sources of information for Hamas.
The Times of Israel reports:
The Israel Defense Forces uncovered a plot in which Hamas members posed as attractive women on social media in order to trick soldiers into revealing sensitive military information, a senior intelligence official said Wednesday.
The Military Intelligence officer would not reveal the exact number of soldiers affected by these attacks, which took place over the last few months, but said it was “many dozens.”
“There is, of course, a potential of serious harm to national security, but the damage that was actually done was minor,” the official said.
The Hamas hackers also posed as army veterans in some of the attacks.
At this point, the official said, the plot is considered foiled, and no additional soldiers have been hacked.
The IDF Blog provides more details, and an example:
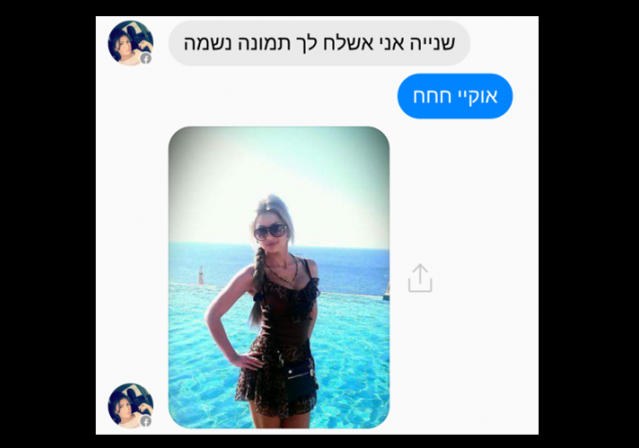
This is Elianna Amer from Ashkelon, Israel. She laughs at your jokes. She really seems to like talking to you. She even sent you a cute picture of her at the beach. Would you video chat with her?
Hamas is hoping that you would, and that you and Elianna will keep talking. After all, she wants to get to know you – and there’s a cool new app that she wants to use to do it. “Elianna” – and the app she’s trying to get you to download – is Hamas’s newest weapon.
Hamas, the radical Islamist terror group, has also been known in the past to use social media to promote terror and incite violence. But the IDF’s Informations Security Unit of the Intelligence Directorate has exposed a new way that Hamas is using the internet to their advantage: the human connection.
Hamas operatives are making fake profiles and trying to persuade IDF soldiers to befriend them. If they can make this connection work, the Hamas operative tries to convince the soldiers to download a virus that turns their phones into the terror group’s own personal information source.
Here are some images from Facebook provided by the IDF (via JPost):
 DONATE
DONATE
Donations tax deductible
to the full extent allowed by law.










Comments
Janet Reno once sent me a naked picture, but someone stole it from my cloud.
Bad visuals there, my friend.
Some brave soul willing to sacrifice his eyes for your sake.
That just a pot, without the honey.
I sent that out on a massive scale to create demand for a new product called Clorox Eye Bleach (TM).
Waiting for the punchline… “Not of herself, of course”.
Clayton Lonetree got snared in a Soviet honeypot and they had to tear down the new US Embassy in Moscow as a result (this was in the 1980’s)
One of those pictures is not like the others.
Not that there’s anything wrong with that. 😉
–Andrew
One of the girls in the first row is wearing a hat. One of the girls in the second row is chewing on some flowers. And one of the girls in the third row is bald and has a goatee.
You really need to be more specific. 🙂
Ok. This is basic social-engineering phishing. It borders on Spear-phishing as a tactical tool, using pretty girls as the lure. The fact that people have to be warned that this exists never ceases to amaze me.
How is this different than the 50+ spam e-mails that show up every week from various “dating” sites? Every week, spam after spam telling me that some pretty young girl wants to chat with me because she saw my message from last week on myspace, friend-finder or any of the other dating sites that I don’t have a membership on or E-bay (pro-tip: I haven’t used my e-bay account to send a message or purchase an item in over a decade, but I DO check it regularly).
BASIC cybersecurity, people. NEVER blindly open a link from someone you don’t know and trust. If you’re getting contacted by someone out-of-the-blue on any Social Media platform, you should be wary and confirm the path of any hyperlink they send you before blindly clicking on it. If that girl seems “out of your league” and immediately seems interested? BIG RED FLAG should be waving across your brain. If you’re getting a link with context from someone you do trust and that doesn’t seem to apply to you, or seems strange from the person sending it, CONTACT THEM before opening.
This is almost as bad as the “Nigerian Prince” financial scams.
Really, if people took just a LITTLE bit more thinking before acting, a large percentage of cyber-intrusion could be avoided.
Ironically, yours is the type of condescending surety most likely to get caught up in a honey trap. Con men love most those who believe themselves unconnable.
No offense, Mr. Skinner, but we’re not idiots.
Actually it’s not hard to be unconnable; as the old saying goes, you can’t con an honest man. Con artists use people’s greed, avarice, and willingness to cheat against them. They probe for weakness, and if they don’t find it quickly, they move on.
In terms of the honeypot scam being discussed, it’s really quite easy – I take it for granted that any electronic “come on” has been sent out by some unwashed 40 something fat man in his underwear. Just hold that image in your mind whenever you are sent something that might look tempting, and you will find it incredibly easy to resist.
That was kind of my point.
We’re NOT idiots. We (collectively) KNOW better.
This story is about how HAMAS was attempting to digitally infiltrate Israeli SOLDIERS, and then to socially engineer them into revealing potentially useful military tactical information, or to turn their digital devices into eavesdroppers.
These soldiers should KNOW BETTER.
By way of example: My Father used to tell this story when he needed to motivate the employees about their role in the organization:
During a visit to the NASA space center in 1962, President John F. Kennedy noticed a janitor carrying a broom. He interrupted his tour, walked over to the man and said, “Hi, I’m Jack Kennedy. What are you doing?” “Well, Mr. President,” the janitor responded, “I’m helping put a man on the moon.”
(Side note: sometimes our business actually WAS making parts for NASA for the Space Shuttle, so it actually was relevant).
People are very often not cognizant of their larger place in the world. That can be particularly dangerous if you’re part of an organization like the IDF when you stop thinking: “What am I doing, and how can my enemies use it to harm me or my nation?” Unfortunately that is the prism that IDF soldiers need to view the world through, because that is what the enemies of Israel want to accomplish. Every IDF soldier has to be cognizant that they are a brick in the wall of Israeli defense.
The thing that is somewhat depressing me lately is that the older I get (and the more criminal defense practice I do) I’m becoming less and less shocked at exactly how many people ARE idiots.
Speaking of Nigerian princes, by coincidence this is today’s Pearls Before Swine
Ahh. Divine Providence….
Surprised they don’t send a close-up of Hillary Clinton’s ankles. That’s got to turn SOMEONE on.
Hello!
“. . . a plot in which Hamas members posed as attractive women on social media.”
“a plot in which Hamas members USED PICTURES OF attractive women on social media.”
(FIFM)