Tech Blogger Finds Proof Donna Brazile Debate Question Email Is Legit
“Specifically, it validates that the HillaryClinton.com sent precisely this content, with this subject, on that date”
Earlier this month, Mary covered the WikiLeaks emails that showed then-CNN contributor, now DNC Chair, Donna Brazile forwarded Team Hillary a question ahead of the second presidential debate. Not only did the DNC not learn anything from the ouster of Debbie Wasserman Schultz, but now, a tech blogger finds proof that the WikiLeaks emails concerning Brazile are not “doctored” as she claimed.
After Democratic Party boss Donna Brazile claimed emails showing her apparently tipping off Hillary Clinton to questions at a March town hall were “doctored,” tech sleuths got to work — and now say they’ve found proof the emails are authentic.
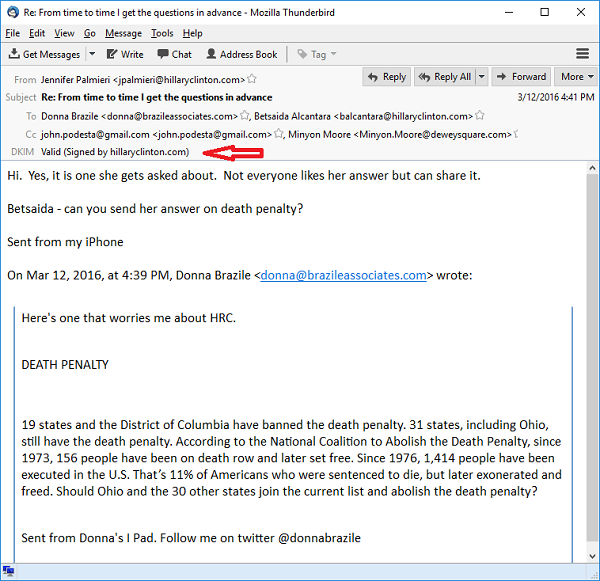
Fox News’ Megyn Kelly questioned Brazile last week about an email that surfaced in hacked messages from Campaign Chairman John Podesta’s account. The email, posted by WikiLeaks and attributed to Brazile, passed on a question to campaign adviser Jennifer Palmieri about the death penalty, under the subject line: “From time to time I get questions in advance.”
The exchange came right before a March town hall hosted by CNN and TV One, where a similar question was asked. Yet Brazile denied receiving questions from CNN.
“I have seen so many doctored emails. I have seen things that come from me at 2 in the morning that I don’t even send,” she said, adding, “I will not sit here and be persecuted, because your information is totally false.”
No one was buying that, so techies decided to look into the emails using a verification program commonly used by email servers to verify emails and sort spam.
Fox News continues:
However, tech blog Errata Security quickly found the email in question could be verified using an everyday verification program.
DomainKeys Identified Mail (DKIM) is a system employed by many email servers, including HillaryClinton.com, to verify emails to recipients and avoid spam filters. The system sends a DKIM “key” to the receiver to verify the sender and confirm the email hasn’t been tampered with.
Consequently, bloggers ran the DKIM keys included in this and other emails through verification software, which in turn validated the Palmieri email as both real and undoctored. The Daily Caller also ran a similar test and got the same result.
In a blog post for Errata Security, cybersecurity expert Robert Graham presented his results, and showed that if the emails had been altered in any way, the software would have declared the email unverified.
“It took less than five minutes,” Graham told FoxNews.com, noting that such software is common and widely available. “It took me longer to document what I had found.”
But could WikiLeaks have hacked and altered the DKIM key also?
Graham says this is unlikely, since to do so they would have needed to access the HillaryClinton.com server.
Some of the newsworthy Wiikileaks emails can be verified with GMail's 2048-bit RSA DKIM keyshttps://t.co/LMjPYrcjhF
— Robᵉʳᵗ Graham?, provocateur (@ErrataRob) October 24, 2016
Graham writes on his blog, Errata Security,
When an email server sends a message, it’ll include an invisible “header”. They aren’t especially hidden, most email programs allow you to view them, it’s just that they are boring, so hidden by default. The DKIM header in this email looks like:
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed;
d=hillaryclinton.com; s=google;h=from:mime-version:references:in-reply-to:date:message-id:subject:to:cc;bh=EHIyNFKU1g6KhzxpAJQtxaW82g5+cTT3qlzIbUpGoRY=;b=JgW85tkuhlDcythkyCrUMjPIAjHbUVPtgyqu+KpUR/kqQjE8+W23zacIh0DtVTqUGDmzaviTrNmI8Ds2aUlzEFjxhJHtgKT4zbRiqDZS7fgba8ifMKCyDgApGNfenmQz+81+hN2OHb/pLmmop+lIeM8ELXHhhr0m/Sd4c/3BOy8=How do you verify this is true. There are a zillion ways with various “DKIM verifiers”.
. . . . Downloading the raw email from WikiLeaks and opening in Thunderbird [the DKIM verifier he prefers], with the addon, I get the following verification that the email is valid. Specifically, it validates that the HillaryClinton.com sent precisely this content, with this subject, on that date.
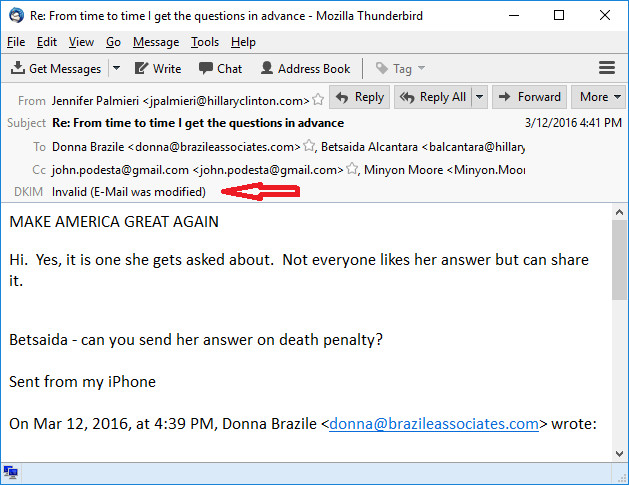
To demonstrate how the DKIM verifier works, Graham added “Make America Great Again” (heh) to the email and received an “invalid” response.
In an update to his post, Graham notes that Hillary’s server is likely to change its DKIM key, so he copied the current one to his post.
Fox News continues:
Graham is so confident in his finding that he has posted a $600 BitCoin challenge to anyone who can alter an email and have it still come up as verified when run through DKIM software.
“If somebody tells you this blogpost is invalid, then tell them they can earn about $600 (current value of BTC) proving it. Otherwise, no,” he says.
Clinton running mate Tim Kaine has also suggested the WikiLeaks emails could be doctored, but so far neither the campaign nor the DNC has presented evidence to support this claim.
DONATE
Donations tax deductible
to the full extent allowed by law.








Comments
OK.
I’m TOTS bummed! You mean to tell me Donna is a big, fat (large boned, anyhow) liar…???
Naw. Naw, naw, naw…
She gives Brazil a bad name, and that is saying something.
Yes. And she can wear yoga pants in public if she wants to, and neither you nor any other patriarchal chauvinist is going to tell her what she can and cannot wear in public.
They might bring back “male chauvinist pig” just for you.
What? Wrong thread?
Wear the yoga pants!
Wow.
An unusually primitive grasp of the concept of Internet security seems to run in the Clinton extended family.
The whole bunch are apparently specializing in being caught with their pants down. Figuratively, in most cases, though in Bill’s, literally.
Still, it’s hard to believe that anybody was actually dumb enough to send stuff like this from the campaign’s official web address. They’re either stupid beyond belief, arrogant beyond belief, or weird beyond belief—so weird that they genuinely think this sort of behavior is perfectly legit.
… though I suppose all three could be true.
You reminded me of something I read this morning?
Madonna has said she will give oral sex to anyone voting for Hillary.
There are reports that someone is already taking her up on her offer. Bill!.
I’m skeptical. Reading descriptions of dkim it’s not clear that it signs the message body, only the headers which would mean the body could be altered.
But I’m not familiar with this technology.
And it does make me wonder. If this is available why would people use pgp signing?
I’m not all that tech savvy, either, Rod, but in the sample he ran to show what happens when the body of the email is changed, he typed in “MAKE AMERICA GREAT AGAIN.” Then ran it, and it came back “invalid.” You can see it in the second email in the post.
I didn’t say that I wasn’t tech savy, I said I was not familiar with DKIM. The very fact that I say that I am not familiar with DKIM shows that I’m tech savy. It’s the unsavy that claim to know everything–it’s called Dunning_Kruger, or as Dirty harry says “A man’s got to know his limitations.”
A couple of points.
First there are a lot of lame people out there who claim to be supertech guys. ( In fact one very good example, the “real guy” that Scorpions is based on is probably a fake. Just like the psychic in “Medium”.) For example read about Aaron Barr and HBGary.
Second there are a lot of demos of things in tech. They don’t necessarily prove what they claim.
As one example, you can go to youtube and find dozens of videos showing you how to get a persons computer password.They are all the same. Run a program which fakes a windows login. What they never tell you is that while such a program helps you compromise computer much further, you already have to have significantly compromised the computer. In other words, they don’t tell you that you have to do the heavy lifting.
I can think of several ways that a such a change could be detected, but would not insure that an email can’t be forged.
It also looks like DKIM is used as a quick way to filter out the worst of spam and phishing attacks, but not to guarantee that an email is not forged.
Believe me, I would love to nail Brazile to the wall, and would love for this to be proof, but I would not be surprised if it fizzles either.
Apparently not savvy enough to google this…
http://www.dkim.org/
A dkim signature validates the entire message. It is used server-to-server to establish trust by ensuring message content is not altered. pgp is used person-to-person for fullblown encryption and non-repudiation.
With the complexity of modern e-mail encoding, it’s actually not that hard to cross-check this way. Each character and white space in the e-mail has a certain value of “volume” of data that it takes up, as well as the formatting of the text itself.
The system then simply takes that “volume” information and attaches a code-key to the e-mail with that information and an original encrypted (effectively) tamper-proof mathematical formula.
If the e-mail is genuine and untampered, the data from the e-mail and the data from the mathematical formula will match. Change so much as one character or space, and the mathematical formula no longer matches and the formula comparing the two returns an error.
Is it ~possible~ to tamper with the mathematical formula? THEORETICALLY yes, but the amount of computing power necessary to discover the adjustment for altering any individual specific character/space is so vast that it’s prohibitive.
So on a server that uses DKIM, the only reasonable way to produce edited emails for (as a random example) a subpoena would be to save them to a file, do the editing, and print them out.
Strange how that is exactly what Hillary’s tech peeps did.
Ah, no. The way you do it is to copy the e-mail storage area onto a hard-drive, and then use any of several commercial programs to open that file and read it. Unless it’s encrypted, you won’t even need a password. (That’s why there are court cases about whether being compelled to provide it violates the 4th and 5th Amendments.)
So Hildebeeste’s only reasons to provide e-mails the way she did was to pre-filter which ones she turned over, and to make it as much of a PITA to actually search through them as possible.
I believe george’s point is that by extracting / printing the emails one could also easily alter the content before printing because the act of printing them out makes dkim validations VERY difficult (if not impossible).
Your point about it being a middle-finger to anyone trying to analyze the emails is also correct.
To go along with Paul’s answer, I don’t remember seeing the DKIM codes on the printouts either, so there’s literally no way to validate any of Hillary’s paper emails. With DKIM, I’m not even sure you could retroactively forge an electronic copy of an email using a dedicated server with the clock set back and a virtual network unless you spent an *immense* amount of time on the project.
Well. You say a lot but it is all meaning less.
Reading up on dkim. It is meant to reduce the traffic of “mal-email”.
To do this, it makes the cost of forging prohibitive. But that’s all relative. To forge an email short key dkim hash takes a laptop 24 hours.
This all makes sense because while you want to stop mal-email, you still want legitimate email to go through cheaply. To add heavyweight encryption would make sending email cost prohibitive.
To stop”mal-email”, all you have to do is make it cost $1 per forgery ( even less ). But people are going to spend a lot more to forge an email from a politician.
Well then, you should be able to collect that BTC reward from Mr. Graham pretty quickly, shouldn’t you.
You’re saying it takes 24 hours? Prove it can be done. Pick an e-mail out of Sec. Clinton’s e-mail pile, modify the text and then modify the DKIM to match and show it as an authentic e-mail.
Besides, I wasn’t just talking about DKIM.
Could this mean that Donna Brazile, a Democrat of the finest character actually lied? No, couldn’t be.
Are you impugning her character?
Are you hoping to be banned for racist, ageist, sizeist, sexist behavior?
Don’t be a hater.
Donna Brazil, at least, did admit well after the fact, that George W. Bush was not guilty of all the charges placed against him over Katrina. But that was quietly, years after the fact.
Dkim.org says the goal is to validate the message itself, and not just the path.
Typical lying dumbacrat!
Does anyone care? Crooked Hillary got away with multiple felonies with the blessing of the DOJ and the FBI.
The DNC chair lying…………….. move alone nothing to see here.