The pro-Assad Syrian Electronic Army hit two more targets Tuesday, after claiming it had hacked the website and database of Viber, an Israeli-based VOIP phone service/messaging application, and the popular internet news site The Daily Dot.
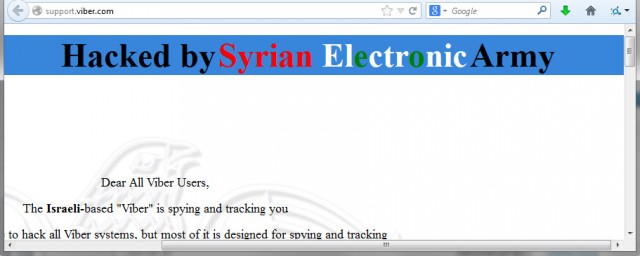
SEA tweeted a warning for Viber users to delete the app, directing readers to the Viber support page, which had been defaced by the hacker(s).
https://twitter.com/Official_SEA12/status/359703368266022913
https://twitter.com/Official_SEA12/status/359867711934836738
At its own website, SEA posted a message taking credit for the hack. The message claimed that the purpose of the Viber app is to spy on and track users. The post also included what are purported to be the names, email addresses and phone numbers of Viber’s administrators.
The Syrian Electronic Army hacked today the website and the database of the Israeli-based “Viber” app
The SEA downloaded some of the app databases
And after we gain access to some systems of that app, it was clear for us that the propuse of this app is spying and tracking of its users
The SEA hacked the support page of the Viber app and uploaded screenshots of one of the app systems in addition to the app administrators names/phone numbers
The defaced support page at Viber initially displayed some of the above information, but now currently redirects to a standard “403 Forbidden” error page (when I checked it late Tuesday evening).
It’s not entirely clear why SEA chose Viber as a target (other than its mention of Israel in connection to Viber).
Also on Tuesday, SEA gained access to the internet news site, The Daily Dot.
SEA had issuing warnings to The Daily Dot from Twitter, demanding the site remove a photo the hacker(s) didn’t like that had accompanied an article about SEA’s recent hacking of Tango.
https://twitter.com/Official_SEA12/status/359326022119854083
Touchy MT @Official_SEA12: Dear @dailydot pls remove attchd pic in this article http://t.co/4nvFcWynye or we'll do something you'll not like
— Mandy Nagy (@Liberty_Chick) July 22, 2013
When The Daily Dot didn’t immediately respond to SEA’s liking, the hacker(s) gained access to The Daily Dot’s website and then taunted them on Twitter.
https://twitter.com/Official_SEA12/status/359553132151336960
https://twitter.com/Official_SEA12/status/359558756746539011
https://twitter.com/Official_SEA12/status/359560293560496130
https://twitter.com/Official_SEA12/status/359563752280047616
As with many of SEA’s previous attacks on other outlets, the hackers gained access to the website, not by way of hacking, but by employing a phishing email while posing as one of the site’s contributors. After one of them clicked on a link that appeared to be sent by a colleague, The Daily Dot explained what happened next.
But the link in that story actually redirects to a site that appears to be Google asking the user to verify his or her username and password. All it takes is a single person who has access to the content management system, and the SEA is in.
Earlier Monday, we sent out a company-wide email asking our contributors and staff members to be particularly careful about clicking on links. Clearly, some people missed the memo.
But the link in that story actually redirects to a site that appears to be Google asking the user to verify his or her username and password. All it takes is a single person who has access to the content management system, and the SEA is in.
Earlier Monday, we sent out a company-wide email asking our contributors and staff members to be particularly careful about clicking on links. Clearly, some people missed the memo.
Worse, we tempted fate. The SEA found this one-liner tossed out by our editor-in-chief in regards to dealing with future threats from outside entities.
That one-liner read, “I’m not sure we should be taking things down when threatened…I mean, I’d like to believe that our hackers are better than their hackers… 🙂 “
The Daily Dot took the incident in stride though, scoring the SEA +1 on that round and taking it as a lesson learned. “After all, the threat of another attack is always looming,” the website read.
https://twitter.com/Official_SEA12/statuses/359558756746539011
 DONATE
DONATE
Donations tax deductible
to the full extent allowed by law.








Comments
By the way, I hope you are keeping the site secure at LI. We have probably got a lot of people angry at us.
So why does Twitter give them an account?
‘Course, we could always bomb them.
Ya gotta go to REDDIT to see this one.
Technologically illiterate MP who masterminded UK porn blocker get hacked, threatens reporter for writing about it
Oh yeah, good one Carol! I saw a related story on the Claire Perry thing earlier.
http://www.guardian.co.uk/media/2013/jul/24/guido-fawkes-threatens-sue-mp-hacking
Someone needs to explain the Streisand effect to her…