How did Hillary’s lawyers search a server no longer in her possession
and which had been wiped clean?

There is a time gap which may hold the key to Hillary’s hide-and-seek email game.
According to the Washington Post and other reporting, a Colorado server company obtained possession of Hillary’s server in 2013, transferred the data, leaving a blank server with no usable data at a storage facility in New Jersey.
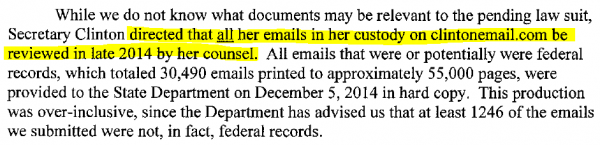
Yet, in a letter filed on August 12, 2015 with the federal Court in the Judicial Watch FOIA litigation regarding Huma Abedin’s outside employment, Hillary’s lawyer, David Kendall. represented that Hillary did not ask counsel to review her emails until late 2014. [Full embed at bottom of post.] He also confirmed that the Colorado company has had possession of the original server since 2013.
* * *
So how could Hillary’s lawyers review a server no longer in Hillary’s possession, and which had been wiped clean?
It’s worth noting that at her March 10, 2015, UN press conference, when a reporter noted that some people suggested an independent review of the server, Hillary did not say that she no longer had the original server or that it had been wiped clean.
Instead, she said “the server will remain private.”
The server contains personal communications from my husband and me, and I believe I have met all of my responsibilities and the server will remain private …
It is that original server that apparently has been turned over to the federal government. Plus a thumb drive, which purportedly only has work-related emails.
If the data was transferred to some other server, where is that one?
On Friday, August 14, 2015, the State Department is required to provide additional information to the Court.
Maybe that will shed some light.
But I’m not hopeful.
Judicial Watch Foia Case Huma Abedin – Defendant’s August 12, 2015 Status Report
Donations tax deductible
to the full extent allowed by law.









Comments
I can spell IT…. and am therefore qualified to ask more questions that are pretty obvious.
Where are:
all the logs from the server (forget about the mail…lets talk about who did what when… including the forensic trail of the Chinese and Russian hackers.
Back ups? Come on…not like we didn’t learn from Lois.
What client devices connected to these servers. Where are they now?
Every other device that connected to these servers.
Every network device in the facility.
Every log from the network service provider.
Don’t tell me Chelsea and her husband adminned all this stuff. There’s shed loads of forensic data here and a pipeline of IT staff that should be getting knocks at the door right now.
I’m also dubious that it was just one server at one location.
Just as she had multiple profiles/accounts, there are additional servers. It’s time for people who think like a criminal who is trying to hide something would think to start investigating this.
The door kickers need to start coming in as hard on the Clintons as they did on the John Does in Wisconsin and the reporters who had their computers confiscated at gun point in the middle of the night.
…I’m proposing one degree lighter than the raid on Bin Laden’s compound.
unless she was using sbs2011 which automatically creates a self signed ssl cert (which she was using) for the exchange server part of it.
I think she was using SBS2011 which is a single box setup and can easily handle tons of email for 75 users, and each user can have multiple email addresses too.
The SW can, but if you were a gangsta like Clinton. Would you put your entire stash on one box in one location?
Hell no. Especially with the nefarious crap she’s running. While you can dismiss Lois Lerner as being not very bright- no so much on the Clinton’s. There were eavesdropping on political enemies cell phones when that was less than trivial to pull off.
Even if there’s no problem with anything Hillary did up to the point of “wiping” the server, that wiping may have ruined any forensic value the server may have had. Even if doing so didn’t cover up any of her own crimes, it may have destroyed evidence of the crimes of others (hackers) and ruined an opportunity to apply damage control with respect to the compromised data. Considering the stakes involved, this error in judgment should disqualify her from any office of public trust.
How do you know it is even the right server?
Well there’s the thumb drives, but that says Kendall’s been engaging in spectacular misdirection of Congress for quite some time. “The server’s clean, everything’s been wiped off it.” With no mention of his personally holding onto national secrets.
The thumb drivers are likely to be where the thumbs of many public employees spend much of their time and, of course, definitely need wiping clean.
The thumb drive(s) they are talking about, are thumb drives containing only copies of e-mail she turned over to the State department – nothing else.
Now, there may be other, super-secret thumb drives not in her laeyer’s office.
Good catch, Prof Bill. I was surprised, too, when I heard that the server went to the tech firm in 2013 because the story didn’t jibe with her obfuscations earlier this year.
Interesting comment on .pst files. Deleting an email out of one does *not* delete the email or make the .pst file smaller, it simply marks the space for Outlook to reuse when it needs to store another email. If this .pst file has not been compressed since the original emails were deleted out of it, they are still there, and in very easy to recover format.
outlook does not use pst for email when hooked to exchange server as she was.
it uses ost file. the ost file cannot be moved and/or imported.
the only pst file may have been manually created archive.
outlook hooked to exchange server does not act like outlook used for pop/imap access, lot of differences and is really a lot more useful.
hit submit too soon.
the reason they provided a pst file is due to them manually creating an archive.
the problem is they can easily control what is in that file and is very easy to hide (not include) damaging items.
Does her lawyer even have security clearance to read the emails? Some are classified.
This is ridiculous. She had a network. The network had multiple pieces of equipment on it at various times. Cabled and wireless. How many drives and when — drives wear out and get replaced. Also backed up. Where are they. “Server” can refer hardware (including the computer case, e.g. the burning picture — which is nothing and apparently is what now is inexplicably “stored”), the various pieces of hardware, and/or the software. It can be partly or entirely “virtual”. The emails landed in various personal computers and devices. There are remnants, logs, turds and other information. There was an upstream provider onto the internet (all email goes through other computers on their way to wherever.) This is the same game that Lois Lerner and the IRS played, counting on public and especially media ignorance.
She needs to be in prison.
They didn’t.
You’ve got to connect the dots.
They searched the new server.
What she turned over now was the old server.
The new server she has still got.
Now a justification for turning over only the old server, I suppose, could be that that was what she was using when she Secretary of State, so that’s the one you want to check for the possibility of being penetrated.
Except for tghe fact that she also has very sensitive information on the second server too, and it would be a problem if it had been hacked into, even if that penetration didn’t happen until 2014.
Of course, also, note, that at the time when the contents were transferred, it might be that some extremely damaging (legally or politically) messages or other contents were deleted.
Various folks are saying the cover-up is worse than the crime … I think Carly said this, some Democrats said it.
But the cover-up is just the part we know about so far. There is a lot of hedging on whether Hillary broke the law or broke “the rules”, but many people go to prison for breaking those rules. And when she dodged FOIA requests by having her own server, and deleted evidence, I don’t see how that itself is not a crime.
What Hillary is hiding may be ten times worse than the cover-up. The $100M that goes to her foundation as she pushed through the uranium deal for her Reset Russia friends, and the other poorly timed tens of millions, and half million dollar speeches … what about all those “personal” emails related to those deals? She keeps rewording her “no classified statements” and she’s now down to “nothing that was MARKED classified at the time”.
Hillary may just be a globalist that believes in spreading power around, or maybe Russia has her emails and uses them coercively. We know Gucifer had some.
There may be some hints and tips in this article on the Clintons and classified intel going to China. It’s deja vu all over again.
http://archive.frontpagemag.com/readArticle.aspx?ARTID=24332
So now we have China somehow getting personal intel on some 24 million Americans working in government, to be used coercively to do more espionage. In the “God Damn America” era, this can hardly be coincidental, nor can the foot dragging on acquiring Hillary’s servers. Our own government lists Christians and returning vets as their enemy, and gives preference to the “diversity” of foreigners. Resist we must.
Absolutely. If it looks like the cover-up was for no good reason, that probably means the cover-up was successful.
No, no, no.
First of all, the Guccifer e-mails that were leaked, were leaked by Russia. If anybody about them was genuine, Ruissia had them.
These e-mails were converted into a special font and all trace of where they really came from was lost. They could be out-and-out forgeries.
Secondly, what that leak from the Russian government claimed Guccifer had, was e-mail FROM Sidney Blumenthal TO Hillary Clinton’s hitherto private secret e-mail address.
It’s assumed, if true, that it was Sidney Blumenthal’s e-mail or computer that was penetrated, not Hillary Clinton’s.
Russia very very likely only knew her e-mail address (which they could have found out 100 ways – she was even business with some probable friends of Putin) and possibly only that Sidney Blumenthal was e-mailing her.
As far as I know, it has not been confirmed that any of Blumenthal e-mails about Libya published in 2013 are genuine.
It’s definitely true that he e-mailed her. But those e-mails – I don’t know.
The Gowdy committee would know if they were genuine, totally made up or altered (well, different from what Sidney Blumenthal supplied the committee) but I don’t know that the committee has said or even leaked anything specifically to that point.
About the time Hillary Clinton’s e-mail address was leaked by Russia, they changed servers.
OK thx. I didn’t know it was not confirmed they were real. And I guess people are just assuming that Hillary was likely to be vulnerable to hacking. But of course that is why having her own server was so wrong.
By the way, even if you adhere to DoD 5220.22-M for data wipe, “TS” rated data should still be handled differently. There is no easy way to actually BE compliant for TS (top secret) data wipe w/o physically destroying the drive. Moreover the physical security of any disk or server with TS on it is fundamentally different. You can’t have it sitting around in a data center like anything else, even if the disks are encrypted. The box has to be physically isolated with separate entry, separate lock and key, CCTV, records of everyone who physically touches it and preferably a mantrap access. Also the physical space itself has its own requirements, eg. CA2 floor to ceiling walls, blueprinted drop ceilings and raised floor space. Logged and inventoried usage of all tools and floorsuckers.
…and logged video surveillance of the room.
With highly classified data, wiping of a drive is typically done merely as a step before physical destruction. Nobody with any knowledge of data destruction would “wipe” and leave it at that.
This has been brought up by others elsewhere, but bears repeating. Hillary has claimed that no classified data passed through her server. Setting aside for a moment the fact we now know that’s not true, if it was true, where are all these other (classified) e-mails, those that were supposedly routed through secure (government) servers?
She never received any e-mail that came from secure government servers. It’s a separate classified system, and can’t e-mail outside.
She has indicated that whenever she wanted to read a classified document, she had it sent to an aide (who might be traveling with her) and had it printed out.
In general, by the way, Hillary Clinton was not one for reading things online. A lot of her e-mail that has become public is a link to something published online, with instructions to print it out.
She also communicated using a Secure Video Teleconference, or other secure means, and in person.
Sometimes, maybe, I read something to that effect – I don’t know if there’s proof, but somebody seems to have undderstood things that way – when her aides wanted to send her a classified document, they edited it to remove the clasification marks, saved it on their hard drive, and then sent it her outside e-mail address.
Mail from her also got to the classified system by being sent first to an unclassified state.gov address of a close aide, like Jake Sullivan, and then was forwarded from a classified e-mail adddress that could be accessed by the same computer as the unclassified state.gov address.
The problem there for her is that removing security markings doesn’t make the information unclassified, but rather just makes the minions doing. such criminals. And it makes her a lier for saying that she never received classified information on her private server.
Apparently, you can’t send already classified information from a classified email system to an unsecured email system like Hillary’s. Which may be where the removal of classified markings comes in. What appears to have maybe happened is that one or more of Hillary’s minions did the dirty work of doing what it took to get the classified material to her on her personal email server. Which requires a lot more intent than merely accidentally sending her classified information.
Now contrast Hillary’s “minor” national defense transgression with the outrageous felony of the “bunglary” of the Watergate, and the prosecution of myriad minor players… ironically, with Hillary Clinton committing even more serious violations resulting in accusations of lying and unethical behavior.
The classic progressive defense of their wrongdoing is “Everyone does it!” sHrillary has already played this card with respect to previous SecStates, but it’s a poor comparison, as no one has shunned use of official government e-mail altogether and circumvented the system and law by setting up an unsecured server.
It will be interesting to see how she plays this card against her Republican opponents. I don’t see how it’s possible, but one can’t underestimate a progressive’s ability to fabricate bogus arguments that appeal to low information voters.
It will also be interesting to see which Republican candidates grow a pair and start hitting sHrillary (and Obama) with appropriate attacks about being lax on the law and on national security.
“If this was on her server and it got into her smart phone, there’s a big problem there,” Baer said during an appearance on CNN International Saturday, noting that the sensitivity of the information reportedly found on Clinton’s private server was likely more secret than what Edward Snowden pilfered.