Vulnerabilities Found in Voting Machines, But Cannot be Fixed by November
Do you know what foreigners cannot hack? Paper and pen.
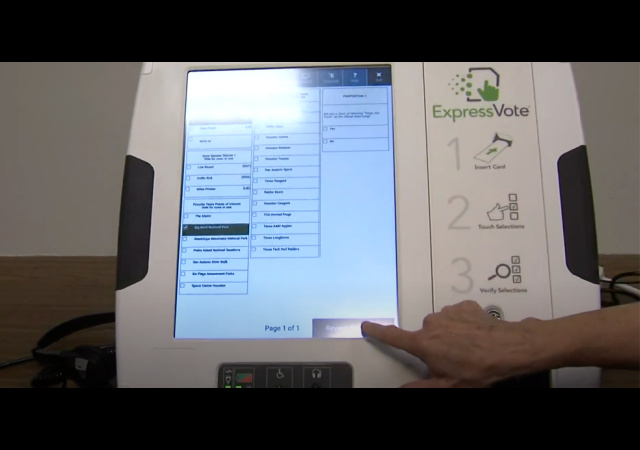
Maybe we should go back to paper ballots. Just saying.
In Las Vegas, hackers attempted to access the voting machines we will use in November to identify any vulnerabilities.
Shouldn’t this have happened MONTHS ago? Because, uh, no one will likely fix the machines before November. From Politico:
In one sense, it’s the normal course of events: Every August, hackers at the DEF CON conference find security gaps in voting equipment, and every year the long and complex process of fixing them means nothing is implemented until the next electoral cycle.
But Election Day security is under particular scrutiny in 2024. That’s both because of increasing worries that foreign adversaries will figure out how to breach machines, and because President Donald Trump’s unsubstantiated allegations of widespread fraud in 2020 undermined confidence in the vote among his supporters.
As a result, many in the election security community are bemoaning the fact that no system has been developed to roll out fixes faster and worrying that the security gaps that get identified this year will provide fodder for those who may want to question the results.
“As far as time goes, it is hard to make any real, major, systemic changes, but especially 90 days out from the election,” said Catherine Terranova, one of the organizers of the DEF CON “Voting Village” hacking event. She argued that’s particularly troubling during “an election year like this.”
The hackers tried to bypass firewalls and security measures in the machines to access voters’ identities and count ballots.
Of course, Politico has to mention RUSSIA, RUSSIA, RUSSIA! No one can accept the fact that no one likes Hillary Clinton. Blech.
“If you don’t think this kind of place is running 24/7 in China, Russia, you’re kidding yourselves,” said Voting Village co-founder Harri Hursti. “We are here only for two and a half days, and we find stuff…it would be stupid to assume that the adversaries don’t have absolute access to everything.”
The hackers hate that it takes so long to fix the machines.
How about they ask officials to move the event up a few months?!
“There’s so much basic stuff that should be happening and is not happening, so yes I’m worried about things not being fixed, but they haven’t been fixed for a long time, and I’m also angry about it,” continued Hursti.
Again, paper ballots:
While there is a robust system in place for certifying voting systems, it’s a long one.
“Even if you find a vulnerability next week in a piece of modern equipment that’s deployed in the field, there’s a challenge in getting the patch and getting the fix out to the state and local elections officials and onto the equipment before the November election,” said Scott Algeier, executive director of the Information Technology-Information Sharing and Analysis Center. The group serves as a way for companies in the IT space to share threat information.
Algeier, who also runs the organization’s Elections Industry Special Interest Group, said the process involves getting sign off from the machine manufacturer, then getting the system recertified by relevant authorities, then going in and updating each device. This complex series of steps is complicated even more by most election machines behind locked down weeks in advance of the elections.
“It’s not a 90-day fix, It’s not a Microsoft every Tuesday, issue your patch and everything works fine,” Algeier said. “It’s a pretty complicated process.”
Others suggested not relying on just one private conference. Instead, bring the vendors and hackers together “in a more formalized setting.”
It happened last year:
The Elections Industry-SIG hosted an event last year in Washington that did just that, and helped to build bridges between a typically suspicious industry and security researchers.
“We want to build a program where we can work in partnership with the security researchers, under the principles of coordinated vulnerability disclosure,” Algeier said.
Until then, for those who packed the Voting Village this weekend, with lines spilling out in the hallway, the event serves a higher purpose.
“We may not be able to fix everything about our election system in the next 90 days, but we can start by getting some of our facts straight and by understanding how our election systems work,” Terranova said.
Again, just use paper ballots. In my technology law class, we learned it’s hard to keep systems updated because once you find a way to block a hacker, they almost immediately try to find another way into the system.
Do you know what foreigners cannot hack?
Paper and pen.
Donations tax deductible
to the full extent allowed by law.








Comments
I am old enough to remember when the Democrats used to rail against the use of electronic voting machines, noting how easily they could be hacked.
Then they suddenly stopped, and embraced the machines.
I wonder why?
You can do a lot of printing between now and the election, as the Democrats know.
You never, ever, ever heard a Chicago Democrat complain about voting machines.
A political story: one time in Chicago on an election night, a young Democratic operative goes in to diddle the machines. He comes out and reports to his old, gray-haired precinct boss that the precinct is going to give the Democratic candidate 4,000 votes and the Republican candidate 0 votes.
The old boss slaps the kid upside the head and says, “youse idiot! Dere ain’t nobody going to believe dat! Youse going to git all of us sent to jail! Now youse go back into dose machines and youse give them Repooblicans,” and he pauses for a moment, “SEVEN votes!”
THIS.
Shouldn’t the machines be programmed to give weight to systemic racism, climate change, intersectionality, and open borders? That would only be fair.
“It’s not a 90-day fix, It’s not a Microsoft every Tuesday, issue your patch and everything works fine,” Algeier said. “It’s a pretty complicated process.”
First of all…
Bullhockey. They obviously don’t understand software, development, or those “Microsoft every Tuesday” patches.
Second, the company itself should be running white hat hacking on their machines constantly. As in, every time they push a new release of code or every 30 days, whichever comes first.
Third, we (the software contract on which I work) push hotfixes in 2 weeks, when necessary. And we’re testing those hotfixes, too. We often get security patches out in less time than that (or face getting shut down).
The hackers tried to bypass firewalls and security measures in the machines
Well, there’s a problem right there: why are these machines connected to the wider internet AT ALL? There is NO good reason for them to be connected to the internet. No, not even for patch updates. Take the drives out and carry those drives to the counting house. Or connect them to a local secure computer and VPN the data to the counting house. (Or, of course, haul those paper ballots to the counting house.) And have an absolutely secure chain of custody for the data.
The hackers hate that it takes so long to fix the machines.
Then DECERTIFY THE MACHINES.
“I’m sorry, no, you can’t use these machines, with this software, for this election. Sucks to be you to scramble to do it somehow else, but here is the restraining order preventing you from using these machines. Guess you should have a back-up plan next year, huh? Maybe you could print up some paper ballots….”
There is absolutely no excuse like “We don’t have time” when it comes to legality. If you can’t figure it out, then maybe you all need to be kicked out of your present positions and let someone else handle it.
Also, voting machines should have REALLY simple software. It’s not that difficult to have a bunch of radio buttons* or checkboxes that record the choices of the user. Nor is it that difficult to then concatenate each person’s data into a long list of data that can then be added up. It requires programming for each election precinct, of course, but you basically have to do that anyway. And all without any real security challenges because you make it a kiosk setup that only runs on the local computer.
Whoops, forgot the asterisk…
(* “radio buttons” are the elements on a web page that allow only one choice from those given. If you click another choice it clears the first choice. “Checkboxes” are when you need to allow more than one choice. And those are moderately easy to constrain to a certain number of choices.)
It’s not clear from the article, but I don’t think this is about voting machines at all, but about the machines used to check voters in, which is why they’re connected to the net, and perhaps also those used to count votes, which shouldn’t be connected.
We are witnessing the Rise of the Unburdened Karen. So many ignorant people weilding power they don’t understand. Damn the consequences, full steam ahead!
President Pete’s election integrity platform:
1) Election Day is a national holiday akin to Christmas. Nothing is open, no business is transacted.
2) Polls are open from 00:01 to 23:59.
3) You must vote in person and only on Election Day.
4) You must provide a government issued ID, and that ID must match the voting roll.
5) Paper ballots only. No machines and no internet access.
6) Purple finger once you’ve finished voting.
7) All counting is done with multiple witnesses from different parties. All counting is video recorded and preserved. All counting is done with 24 hours of the polls closing. Anything not counted is considered null & void.
8) Conviction of election fraud is punishable by death. If you think that’s harsh, look at the worldwide carnage as a result of the 2020 steal. I’m telling you, it would only take a lethal injection/electrocution or two to dissuade these traitors.
Ok, as an alternative, I’m amenable to building a traitors SuperMax prison in Alaska. 6×6 concrete cells, no windows. Polar bears… have to incorporate polar bears somehow.
Pretty much a minor variation on what I’ve proposed for years.
All polling stations open the SAME 24 hour period. No account for time zones, that way every station closes at the same time.
I like the purple finger…even better would be to dip your finger in either red or blue ink that would leave two easily identifiable marks…one for the ballot, the other for society.
I do not like #1. You certainly can’t stop a lot of folks from working that day. (Not everyone’s jobs entail retail transactions.) And there’s no reason most people can’t simply work it into their schedule. For everyone else, there’s absentee balloting.
As to #3, I do want absentee balloting available. You go in person to the voting registrar’s office and vote before you leave town. If you’re in the military, the precinct should contract with the voting office on base to have the members vote in person with them.
(I have absentee voted once since living in this state. I was a contractor with the military and would be at sea over election day. I went in person, showed my ID, got checked off the list, was handed a ballot and was pointed to the lone voting “booth” in the office. Once I had voted, I returned the ballot and they checked everything, sealed it up and stored it properly for election day.)
IMPRESSIVE! HOWEVER, I see a TINY FLAW in your plan! Nowhere do you discuss the ENTRY POINT into the POLAR PRISON! Way back in 1988 I took a job and one of the first persons I worked with had a rather simple solution for dealing with DEPORTATIONS of ILLEGALS! It involved a trebuchet! His idea was to have the WALL with NO DOORS and use the trebuchet to just “toss” them “gently” over the wall! As far as “incorporating the polar bears”, just let the prison be a “free range” prison – no bars – no doors!
The paper ballots must have anti tamper and anti forgery features along with a know number issued to a precinct. All ballots must be accounted for when the day is over. Voted, Unvoted, and Spoiled. Treat this like money.
Treat this like money.
^^^THIS^^^
That’s already the case. At least in NYC, and I’d be astonished if it’s not the case everywhere.
But it’s impossible to guarantee that everything will reconcile exactly. For instance, it’s possible that a voter is issued a ballot, and rather than voting he walks off with it. You can’t prevent that. At the end of the day the reconciliation will be out.
I’ve recommended the same, but wanted a silver nitrate solution. Can’t wash it off – soaks int the epidermis and turns dead black in the sun fast or more slowly under indoor lights (chem labs past). the epidermis plus a bit has to wear off.
Add to that, completely purge the voter rolls after every Presidential election. Re-enrollment is required to vote. Pretty easy process.
No. First of all, where the hell would the fedgov get the authority to mandate that? Second, even if it were technically constitutional, are you seriously proposing to ban people from earning a living that whole day?!!! What kind of tyrant would do that on any day? And no, Christmas is not like that. There are plenty of businesses open then, and no law prevents anyone from working if they like.
I don’t think it’s possible to count all the ballots within 24 hours. One major reason it takes longer in the USA than in most countries is that most countries only have one race to count. If there’s a second race, it’s on a separate ballot and isn’t counted on election night. Here we hold all our elections on one day, so there are many races on the ballot, possibly a dozen or more, plus referendum questions if any.
“Maybe we should go back to paper ballots.”
“The Virginia model for Election Security works. This isn’t a Democrat or Republican issue, it’s an American and Virginian issue. Every legal vote deserves to be counted without being watered down by illegal votes or inaccurate machines. In Virginia, we don’t play games and our model for election security is working. … We use 100% paper ballots with a strict chain of custody. We use counting machines, not voting machines, that are tested prior to every election and never connected to the internet. We do not mass mail ballots. We monitor our drop boxes 24/7. We verify the legal presence and identity of voters using DMV data and other trusted data sources to update our voter rolls daily, not only adding new voters, but scrubbing the lists to remove those that should not be on it, like the deceased, individuals that have moved, and non-citizens that have accidentally or maliciously attempted to register.”
~ Governor Glenn Youngkin Issues Executive Order to Codify Comprehensive Election Security Measures to Protect Legal Voters and Accurate Counts,
https://www.governor.virginia.gov/newsroom/news-releases/2024/august/name-1031585-en.html
And I’ve never (in 23 years) seen anyone grouse about having to show ID to get their ballot. At some point, Virginia did use voting machines. Lots of people hated them, so they didn’t last.
Something like this should be a law for Federal elections, with funds for implementation included.
Should be. Irrationally this is nearly the exact opposite of the bill the Dems have been working on for 8 years.
If Youngkin manages to actually implement this Virginia will go red.
It’s SOP whenever the voting process manages to undermine leftist cheating.
It always goes red.
No, it won’t. Virginia is purple because of the government employees and contractors in northern Virginia (which goes at least as far south as Fredericksburg, now) and the dedicated Democrat minorities in Richmond and the Tidewater area. Places aren’t blue just because of cheating – it’s usually because of the people there.
And while he did a nice executive order about this, most of it is already the law and has been for some time. The only change that came from his order was the purging of the voter rolls (which is also already law, but it needs to be ordered done).
Virginia is purple because Democrats cheat.
There are places that have a preponderance of Democrats, and Democrats cheat there as well.
Because they don’t believe the democratic process is valid.
No, Virginia is purple because it’s full of socialists and progressives. It’s full of people who believe in big government.
Sure, there’s some cheating going on, but Virginia doesn’t go full Democrat every so often because of cheating. It’s because that’s what the people here actually vote for.
EVERY computer is always vulnerable because they all rely on unverified technical software (compilers, assemblers, even microcode assemblers) that itself can’t be verified for the same reason. It’s just a matter of motivation whether somebody bothers to hack them. Voting supplies really high motivation to hack.
Slightly technical but not bad details in Ken Thompson’s Turing lecture “On Trusting Trust” back in the 70s or 80s.
This is untrue. I am a software tester. And I can verify it by putting information in across the design space and test the output. If it doesn’t match, then the code is bad or wrong. PERIOD.
And, once the code is deployed, I test it again. And if it’s different from the test system, then it gets rolled back until we find out why there’s a difference.
If you “roll your own” compiler, sure you can cheat. But that’s why you use industry standards. If the compiler doesn’t compile in the way you expect it to, then the compiler will get junked. Because it will affect EVERYONE the same.
Hacking only applies to changing the code or database entries after it’s deployed. With proper security that won’t happen (without aid from the process or machine owner). But that puts it back in the realm of “a human must use their granted access to cheat.”
You can test your software. Are you also running the same validity test on the microcode of the processor or the operating system code or the compiler code? Are you rerunning those tests every time they come out with a new generation of processor where they patch the operating system with a compiler has a new version?
Huh? By definition, yes. Because if that new processor comes into the hardware for my system, it gets tested again. (BTW, remember the x486 error way back in the early aughts? Yeah, we found that it affected some of our software because we tested it the next time we did a release.) We test the system every time a Windows or Linux patch comes out, and every time there’s an Oracle patch, and every Java patch.
BTW, if you change the microcode, the people doing that have to test extensively because it will be immediately apparent if it f’s things up in the field. Intel is dealing with a problem in some of their CPUs right now because they allowed some overclocking to occur that basically ate through the chip. That affects almost EVERYBODY.
No, I actually don’t test the software with every possible chip or permutation. Because – exactly like the voting machines – our software runs on certain hardware. If we were to upgrade the machines on which it runs, I would absolutely run tests to make sure the new hardware doesn’t screw something up. And, if I worked on consumer software, that was intended to be used across the spectrum I sure as heck would test it on a bunch of different hardware.
Your last sentence doesn’t make any sense, grammatically, as typed. But I think I got the gist.
No computers for voting or counting. Paper ballot and hand counts. I don’t care if theyve been vetted, or they use open source. Code Obfuscation is a thing where by the goal of the programmer is to write code that does a thing in a very very non-obvious way, even for other coders to see. Expect that to happen with these devices, They have contests.
https://www.ioccc.org/
“Programmers sometimes obfuscate source code in order to make it harder for humans (but not computers) to understand it. For instance, insofar as JavaScript code is often executed client-side, a programmer might want to obfuscate it in order to protect their intellectual property. And some people like to obfuscate code just for fun! Obfuscation itself might involve eliminating unnecessary whitespace and shortening the names of functions and variables to be nondescript, essentially adopting (very!) bad style.
But obfuscation really just makes it harder, not impossible, for humans to understand code. With enough effort, code can be deobfuscated too. (Of course, it might be less effort just to rewrite the same code from scratch!) Let’s convince you of such.
For each of the obfuscated functions below, state what it does and, in no more than three sentences, explain how it works. Assume that any requisite libraries have been included (elsewhere). You’re welcome to copy/paste the code into VS Code in order to style and experiment with it.”
https://cs50.harvard.edu/college/2021/fall/test/obfuscated/
Not too long ago voting machines were mechanical. You rotate a lever next to the candidate’s name. A gear would turn and the odometer-like counter in a sealed case would turn the next number. At the end of the night a human would unlock the back panel and tally up the numbers under each column. Then a second and maybe third human would follow and count. They would compare notes and do it all over again if there was a mismatch. It took all of five minutes per machine.
Think today’s Democrat has even the slightest chance of winning against that system? That’s why they disappeared. Technology making it easier? my rear end.
That is utterly and completely backwards. Those machines were very hackable, because there was no audit trail, no possible way to verify anything. You had to trust the machine, and that it had been set to zero at the beginning and hadn’t been fiddled with. There were no ballots, so no way to do a recount. And they were concentrated in D strongholds, so we know the Ds were using them for fraud.
dnc:
it depends how you define
vulnerabilities
There is absolutely no excuse for closed-source voting machines being used in this country. We know that companies, like government agencies, are subject to ideological capture.
All voting machines should run on open source software, which would allow anyone to see exactly how it works, including whether or not it has functionality that would allow election workers to move votes around.
I’m also open to the argument that voting machines should not be used at all.
Access to source code doesn’t solve it. The computer doesn’t necessarily do what the code says it does.
true, and I saw your earlier comment about voting systems providing massive incentive for the most high-tech (ergo costly) of hacking schemes. it’s certainly a strong argument for having no computing-based voting tech at all. voting in general, and voting machines in particular present an absolutely massive threat surface.
That’s crap. The computer is not a thinking entity. If you don’t write crappy code, it’s a determinant system. It does what you tell it to.
(As a matter of fact, one of the famous axioms of computer programming is “Computers don’t what you want them to, they do what you tell them to do.”)
*don’t do what you want them to
Not necessary to “forge” paper ballots.
They can just throw out paper ballots that were cast for the rival candidate.
IT’s time to “VIRGINIANIZE” the elections! Paper Ballots, PROOF OF CITIZENSHIP, PROOF OF IDENTITY for Mail Ins, and HARSH PUNISHMENT for offenders!
Mechanical voting machines. COmmittees including dems, republicans, and some independents recording the results when the polls close. The numbers phoned in to the state board, with paper back-ups driven in. DONE.
And NO MAIL-IN BALLOT BULLSH*T!!
You can never have any voting integrity with the laughable mail-in ballots and anonymous drop off boxes. Just the idea that anyone would allow this crap is INSANE!!
Paper and pen are not immune to manipulations.
True, but the distributed nature of our election process means that ‘moving the needle’ in a significant way would mean corrupting the process in a large number of voting precincts, and in a manual-voting system this would mean lots of opportunities for this fraud to be spotted. But electronic machines present a unique opportunity for such fraud to be done in a centralized manner, potentially impacting things on a massive scale, all while being hidden from plain view.
But electronic machines present a unique opportunity for such fraud to be done in a centralized manner
Only partly. Either through manipulation of the code/databases so that the inputs do not match the outputs (which should be caught in testing), or through being networked with poor security.
It’s why I argue for non-networked machines – at least not networked to the internet, and I’m not sure they should be networked at all.
And any updates causing problems can easily be caught by adequate random testing before voting commences.
If they were examined as closely as Florida’s chads by 3 people sitting side by side, it would sure be damn tuff…
Corrupting the process in a large number of precincts, exactly as was done in 2020 against Trump?
But it’s a lot harder to hide them. And there’s a person (or people) directly associated. You can send them all to jail, as opposed to “something happened inside the black box.”
Nothing is immune. But the more complex thing is the easier it is to corrupt. It’s much harder to mess up simple things
Especially if that complexity is inside a black box.
It’s the ‘American syndrome.”
Like the old story: NASA spent large sums to develop pens that wrote in vacuum and zero gravity. Russian cosmonauts used pencils.
Soooooo do you have the best and brightest of all computer programmers write unhackable code who were just the ones last night at your local Antifa riot tossing Molotov Cocktails?
These are the same geniuses who just a few months ago brought us the AI computer when you searched for imagines of WWII German Soldiers they were black.
Garbage in, garbage out.
First of all, if you can “hack” a voting machine remotely, that means it’s connected to the internet which should never happen. There is not one good reason to ever connect one of those things to the internet, not even for software patching. Though the software should be so simple it shouldn’t require much in the way of patching. The back-end is literally incrementing one column and only one column at a time. There is no need for floating point math as you will never have a vote that is not a whole number value. Not integers, whole numbers, as you will never have a negative vote.
In fact, the ideal solution is simply printed ballots you mark with a pen and the ideal tabulation solution is to publicly count votes with multiple witnesses and then to write down and hold the final tallies until all other precincts have completed their tallies. Final tally is done when and only when all precincts are complete.
As for absentee, that should be arranged ahead of time and it should be only for valid reasons. You should have to register for an absentee ballot in person with photo identification. For military personnel, arrangements should be made through their branch of the service as they have a very valid reason for not being able to vote in person. All other voting should be in person, on the day as there are already legal requirements for employers to allow their employees an opportunity to vote. A national holiday for election day would be ideal, but some things do need to run no matter what.
The best solutions are simple, because simple things are much harder to corrupt than complex things. Incrementing columns one at time is not a complex thing unless you make it so, and if you are making it so then you have an ulterior motive.
The back-end is literally incrementing one column and only one column at a time.
Not entirely true, depending on your view of a database update query. It should update multiple columns near simultaneously, depending on how many elections are on any single ballot.
More of a quibble than an argument.
I think most of the complications they are introducing are because they want a single bit of software into which you load some election parameters, and every precinct now has its machines creating the “ballots.” So, they are using a giant black box that does a bunch of funky stuff to generate lists and permutations and so forth, to display to the voter. And once you do that, there are LOTS of things that can go wrong (or go as intended). There are also vulnerabilities in using that sort of black box setup, as there are inevitably windows and doors into the box for developers to use.
The best solutions are simple
Amen.
as a member of the military for 20 years.. I was home for exactly 2 elections. everything else was by absentee … write to S.O.S
get ballot fill out and mail back.
took about 2 weeks depending where I was … some longer then others. AdaK AK about 8 days
Japan about 15 days Diego Garcia BIOT. 20-25 days (maybe depends on the mail) so I’m all in favor of voting on Election Day only except for absentee ballots.
I can remember my first time voting
go into booth. pull lever curtain closes. make choices by clicking down a red lever next to who or what
you pick. do until all choices have been made. pull lever curtain opens and punch card is complete.
not sure why they got rid of it. was simple and it worked. that is probably why they got rid of it. :<
Punch cards have issues with sometimes not completely punching through. Then, of course, if they’re handled badly you can get bogus punch throughs. It’s what the hullabaloo in Florida was all about in 2004 – remember “hanging chads”? They got rid of them because NOONE wanted to be the municipality that went through that again.
Even those were hackable. They used odometer style wheels. Cheaters would preset the wheels with extra votes for their candidates, then paste stickers showing zeroes on the numbers that should be showing through the window. The stickers would rub off and drop away when the wheel turned, so nothing looked off.
“Even if you find a vulnerability next week in a piece of modern equipment that’s deployed in the field, there’s a challenge in getting the patch and getting the fix out to the state and local elections officials and onto the equipment before the November election,”
And then every blue moon you get a “patch from hell” like Crowdstrike’s, and you end up having to pretty much “rebuild civilization” from scratch.