Internet security expert: “We believe this attack was just a test, and more attacks will come”
“We feel strongly this was NOT an attack from another country, but a group of loosely organized hackers”
A Legal Insurrection reader who I know to be involved in internet security issues sent me the following explanation of yesterday’s attacks that slowed down many major websites. That person asked to keep his name private because of his work position.
Here is his explanation sent to clients of the firm he works at:
Our entire senior technical team and I have read through the intelligence on the DDOS attack today against DYN. It resulted in massive internet outages on the east coast and eventually the west coast. This was actually several separate escalating attacks.
This type of attack was very predictable because of the recent public release of the Mirai DDOS Malware. The attack consisted of millions of bogus requests to the servers at DYN. All servers and clouds have finite capacity and eventually the servers at DYN failed. DYN provides DNS services for thousands of websites (Twitter, Spotify, Amazon AWS, Amazon Ads, Reddit, Paypal, and other big players).
If you are unfamiliar with DNS, you can think of it as a phone directory for the internet. When you type in a domain name, your ISP (internet service provider) uses the DNS (domain name service) to convert the name to an IP address, which in turn is used to route your request. If there is no DNS, there is no way to route the request and the website is unreachable.
This attack has much bigger ramifications than most people know. Here are the things you need to know:
1. DYN should have been prepared for this attack. It is unclear why they were incapable of absorbing it or mitigating the risk of such an attack. They are a huge company and one of their experts (Doug Madery) made a presentation on this subject yesterday (which no doubt triggered the attack).
2. DYN claims to have mitigated the attacks and then the attacks subsided. We are skeptical as to whether or not they mitigated the majority of the impact, before the attacks stopped. To reassure their customers they would need to release the statement they did.
3. There is no way to determine if they will be attacked again and what steps they are currently taking to protect themselves.
4. No data was at risk at any time and no sites were hacked. This was simply a flood of fake traffic that crushed the DYN DNS server cluster.
5. We feel strongly this was NOT an attack from another country, but a group of loosely organized hackers (internet sociopaths).
6. This attack was orchestrated through the software vulnerabilities of the IOT (Internet of Things). These are NOT infected PCs. Instead, they are infected devices such as webcams, security cameras, DVRs, smart TVs, routers, and similar devices.
7. There is no quick fix for this. You would need all the owners to update the firmware of the devices.
8. The last attack may have used as many as 500,000 infected devices. That is probably a very small fraction of the infected devices.
9. It is impossible to block the IP addresses of the devices, because the real IP addresses were not used (known as IP spoofing).
10. The malware takes advantage of the practices of certain ISPs (internet service providers) that do a poor job of blocking this type of traffic.
11. The attack on DYN was an obvious choice because they provide the DNS for Twitter, Spotify, Amazon AWS, Amazon Ads, Reddit, Paypal (and other big players) and had just publicly shared their concerns about this vulnerability.
12. Your site was NOT directly affected, because the DNS is hosted on our private DNS servers or your host (too small to be targets)
13. If you had third-party elements on your website that were affected (Twitter widgets, ads, etc.), the pages would have seemed slow to load
14. This attack could have had ANY target. Use your imagination as to what other targets could be (airlines, transportation, government, major news sites, etc.).
15. The ONLY long term fix is to have major internet players (Google, Facebook, Twitter, etc.) threaten to block ALL traffic from non-compliant ISPs.
16. We believe this attack was just a test, and more attacks will come (most likely on different targets).
 DONATE
DONATE
Donations tax deductible
to the full extent allowed by law.








Comments
Some have been saying that this is not something new (although I suppose their success in actually taking something down is new) and has been going on for quite some time.
https://www.lawfareblog.com/someone-learning-how-take-down-internet
I suppose the question is, who, if not a state and so on. It seems that is the more interesting part of the story: how the security firms can be confident that it is not a state (or state-like, say for example ISIS, though that is doubtful) and instead is a “loose collection” of hackers.
Dry run by the Obama Administration, intending to make it appear it was done by hackers. All in anticipation of a Donald Trump election victory.
Extreme Narcissists like Buraq Hussein Obama don’t give up the wheels and levers of power willingly.
It took two million Soviet Soldiers on the streets of Berlin overhead going street by street, block by block, house by house, room by room looking for him before Hitler decided it was time for him to check out.
Based on my own (admittedly not quite encyclopedic) technical understanding, this is the most likely cause.
The DOS theory is untenable, for reasons already discussed (as well as others I didn’t mention earlier since my fingers were sore from typing). Therefore, it’s most likely just cover.
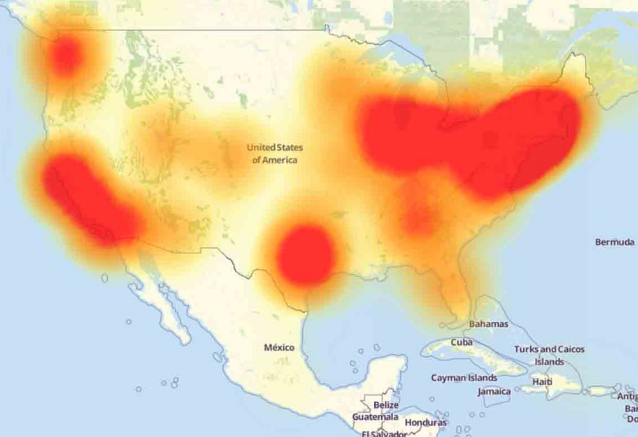
Most alarming were the maps everyone had posted yesterday, showing blackout hotspots in the Washington-Boston corridor, and Texas. (The maps are busier today, and that obscures the essential features.) It’s the Texas one which should set off the alarm bells for anyone involved in the Internet biz. Lots of big server farms in Texas. (My own websites lived on a server in Texas until my hosting company moved them recently.) That says it’s not a software problem; that would be more diffuse, and distributed over a larger area. It’s hardware. Somebody’s been pulling plugs, and the rest of the network bogs down as it takes up the load.
Somebody really is experimenting with a kill switch. And my guess is that the server farms are in on it, possibly after threats of harassment by the DOJ. If that’s correct, they are not going to admit it. They’ll spread some other story instead … maybe something about DOS attacks.
Final takeaway? The Democrats expect to lose this election, and are preparing Plan B.
I’m in the tech field myself, and I see no reason that neckbeards living in their mothers’ basements couldn’t pull off a DDoS of this scale. They do this thing all the time, but it’s not normally directed at the backbones of the internet like DNS services.
If Obama really wanted a kill switch for the internet, he wouldn’t have handed over the keys to the kingdom to ICANN.
Irrelevant, once you realize that this was no more a DDoS attack than Hillary’s problem on September 11 was pneumonia.
I’m certainly not arguing with you, but may I ask what evidence you have that this was not a DDos attack? Are you saying that this was not due to a trojan infecting lots of webcams, TVs, etc?
what evidence you have that this was not a DDos attack?
The evidence is that the reported symptoms would not be caused by the disease being blamed. Just as lung cancer doesn’t cause your nose to fall off, a DoS attack won’t affect the Internet DNS system. DNS is not subject to the same vulnerabilities as individual websites are. A name server comprising part of the DNS system can be attacked with a DoS attack, but that won’t inhibit other servers’ ability to find web site addresses.
A classic DoS attack ties up a site’s server with a bunch of rubbish requests. The server still functions, but it’s not smart enough to know which incoming requests are rubbish and which are real until it tries to deal with them. So legit requests are stuck waiting along with the rubbish ones. This slows things down, potentially by many orders of magnitude. Imagine eBay doing a search; you type a search term into your browser, hit “enter”, your browser asks your ISP’s server to send the request to eBay’s server. eBay’s server takes the search term, performs the search, composes the HTML to display a web page showing search results, and sends that back to your ISP’s server and then to your browser. If this all takes a tenth of a second, no problem. If it takes ten seconds, you think something’s wrong. If it takes a thousand seconds (over a quarter of an hour), you give up and do something else. But eBay’s server is working just fine, generating search result web page HTML as fast as ever; it’s just taking a long time to get to your request. Hence, the attack—that is, bombardment of eBay’s server with tens of millions of rubbish requests—is called “denial of service”, though it should more accurately be called “delay of service”.
But DNS doesn’t work that way. Unlike your communication with eBay’s server, your computer doesn’t have to go to a specific server to get the information it wants. It can get it from any server which happens to have the information. The original source of that information, the address of the web site you’re looking for, ultimately comes from an “authoritative” name server. That’s one of the name servers the site operator sets. I’ve never worked on a web site which had fewer than two name servers; they can have far more. The name servers tell every other server in the network which wants to know what the web site’s numerical address is; i.e., where to find it. The authoritative name server isn’t important to this process, except that it’s the final word on the site’s address; when it’s set, eventually all other interested servers will get that address—basically, by diffusion—and can pass it along to other servers when needed. If your server gets an obsolete address from some other random server, you get one of those “cannot connect” messages. Hit reload, your computer tells your ISP’s server to try again, and it gets some other computer which hands it another, and maybe current, address, and you successfully connect.
The DNS system is hierarchial, which allows addresses to be updated; a site operator can change his site’s address, and that information will eventually propagate to all other servers which are interested. But to get the address information, it’s not necessary to go all the way to the top of the hierarchy. Your server asks other servers more or less at random until it gets the answer it needs; then it stops asking, and goes to the address it finally found. This is why the system can withstand tremendous damage; a site’s authoritative name servers can be destroyed, but other servers can still find the address they need; and, assuming the site’s server wasn’t also destroyed, these other servers can then connect. Half of the Internet could disappear, but the remaining half would still function. DoS attacks on a site’s nameserver do not prevent other servers from finding the site’s address.
Which is why I think the DoS explanation is bogus, even if a genuine DoS attack was staged at the same time.
Thanks for the great explanation, Tom. It makes sense. So if it wasn’t DDoS, what caused all those sites to be unreachable?
My guess? (And that’s all it is; sheer speculation.) Somebody’s physically pulling some plugs—disconnecting a few data centers from their phone lines (they all have multiple T1/T3 lines, leased from different vendors so they don’t go down if one of them has a strike), turning off the power switches on a few select servers…. Simple stuff, but it’s not software-controlled; it would be done by a local human agent. When everything’s hooked back up and powered again, the network would immediately go back to normal operation, with no sign of the temporary outage. There will doubtless be logs showing it all, but they’re private internal operations stuff and nobody’s going to publish them.
Data centers are not going to do this on their own. It’d be bad business as well as very unprofessional behavior. But somebody in the Administration could be suggesting that they might want to be co-operative. You know, because of racism, or terrorism, or something.
And why might the administration be interested in such a thing? Control. The only means of mass communication not essentially controlled by the Dems or the Feds is the Net. The Feds can control the medium, in a heavy-handed way, but not the message. So, postulating a scenario in which very large numbers of people opposed to a particularly heavy-handed government action might be able to coordinate their activities via Internet, it would be to the government’s advantage to turn the thing off for a while.
The scenario could be, say, reasonably clear evidence of colossal voter fraud, and a declaration that candidate X is the winner. Rather than letting them get away with that, Candidate Z might consider a call for some sort of action by his supporters, which could be a crowd of, say, 100 thousand (a bit over half of registered US voters). As examples of what such a crowd might do to oppose or paralyze a government, consider the nuthold Alexander Scargill of the coal miner’s union had on Britain until the Thatcher era; or similar strike-style “action” which is always looming in France. But, with no marching orders, nothing will happen.
Cut off the Internet, and you cut off the orders.
Again, this is all rank speculation.
D’oh!
100 million voters, not 100 thousand.
Another scenario; the Admin would love to plug the Wikileaks e-mail dumps. It can rely on the conventional press to smother them, but it can’t control an Internet dump … unless it turns off the Internet. Yes, the business disruption would be serious; airlines, train schedules, Wall Street would be very confused for a while … but someone else’s inconvenience isn’t all that big a concern when Obama’s “legacy” is at stake.
And yet we seem helpless. A feature of the neoliberal order is that the state’s function is to serve as clearing houses for multinational business transactions—citizens, borders, and cohesion beyond accepting some form of state subsidized peonage is secondary.
The neoliberal order deals with threats through non-recognition: acknowledging as existential things like jihadis, cross border drug flows, destabilizing migration, or cyber war also implies the need to action, and action unsettles commerce. Best to absorb the costs and convince the rest of us that it’s all part of some “new normal.”
It’s an internal contradiction within the current system that will eventually lead to its collapse—the ruling orders’ belief that it can absorb anything as a cost of doing business.
Thanks for posting this, Professor. I just configured my computer to use OpenDNS in the hopes that it might help if this happens again.
God that explanation is so terrible…
There is a phrase “not even wrong” that comes to mind.
Let us begin with what DNS is.
If I tell my network card “I want to connect to legalinsurrection”, it replies “what is that”.
So if I want to connect to legalinsurrection, I tell my computer. My computer connects to my ISP’s nameserver ( which I have to configure my computer to access ). My computer then sends a query to the nameserver “where is legalinsurrection?”. It replies “72.10.36.21”.
My computer then tells my network card “I want to connect to 72.10.36.21”. At that point I am connected to legalinsurrection.
Now when I ask my ISP’s nameserver what the address to legalinsurrection is, it tries to lookup the address in it’s tables. Most likely it’s there, but if not it sends a request to the namesever up next in the hierarchy. So the request goes upa “chain of command” till you get an answer.
DYN runs a bunch of the nameservers high up in the hierarchy.
What happened was that a bunch of internet enabled devices–baby monitors, refrigerators, lighting systems, microwaves — not routers, DVRs or any of the devices you list — those are too sophisticated to be considered IoT, these devices where infected using some exploit, they were then used to keep calling the DYN nameservers. As a result the DYN servers were so busy answering these false requests, they could not also answer the legitimate requests. This is what DoS means.
Now because the nameservers were too busy, when my requests for legalinsurrections IP (72.10.36.21) went up line I got put on hold. So effectively a large chunk of the internet froze.
The devices that were infected are not PCs but they are more powerful then 1995 PCs runing Windows or MacOs. Most important. Most are still infected. By their embedded nature the vulnerabilities are almost impossible to fix. Companies like Samsung no longer update the software on their phones after a year. Do you think they can and will update the software on a five year old refrigerator?
Was this preventable? Maybe. But if they got enough devices then probably not. The best they can do is force the attacker to use more devices in the attack.
Did this do any damage to any systems out there? We don’t know. A little of DoS attacks are smoke screens to hide other attacks ala “Two minute warning”
spoiler warning for the movie “Two minute warning”
In the movie Two Minute Warning there is a sniper at a pro football game who starts shooting up the crowd at the minute warning. This causes a panic, resulting people running in the streets causing chaos. In the meantime a bunch of thieve break into a museam and steal the art using the panic as a screen.
End of spoiler.
Was it state sponsored? Probably not. The way I would advice a government to do such an attack is to build a mini-internet for under $100000 and run simulated attacks on that. That way people won’t be alerted to the vulnerabilities and move to fix them.
One more thing. Because they use IoT devices, which are not likey to have their firmware updated to eliminated, and because they proliferate the attacker gets that much more of an attack.
The fraud of “Barack Hussein Obama” was also a test run. The Hillocaust to follow is the real thing.